TLDR;
This video discusses various aspects of cybersecurity, including hacking techniques, data protection, and online safety measures. It covers topics such as the dark web, wiretapping, secure messaging apps, and vulnerabilities in mobile devices. The speakers also share tips on how to protect personal data and avoid becoming a victim of cybercrime.
- The dark web is not as crazy as people think.
- Monitoring data package usage can help detect if a phone is being tapped.
- There are no preventive measures to avoid wiretapping.
- Regular calls and SMS are not safe.
- The safest application to prevent wiretapping does not exist.
- It is not recommended to sell your cellphone.
- Meta has used unique methods to monitor competitors.
- It is not true that cellphones are listening to conversations.
- Data leaks are dangerous because they provide criminals with more information.
- It is important to ask what data is for when providing personal information.
- Neither iPhone nor Android is guaranteed to be safe.
- The smallest hacking tool in the world is Fliper Zero.
- In the era of hacking, the safest place to put your money is in a bank without e-digital banking.
- The easiest way to prevent social media accounts from being hacked is to activate two-step verification.
Intro [0:00]
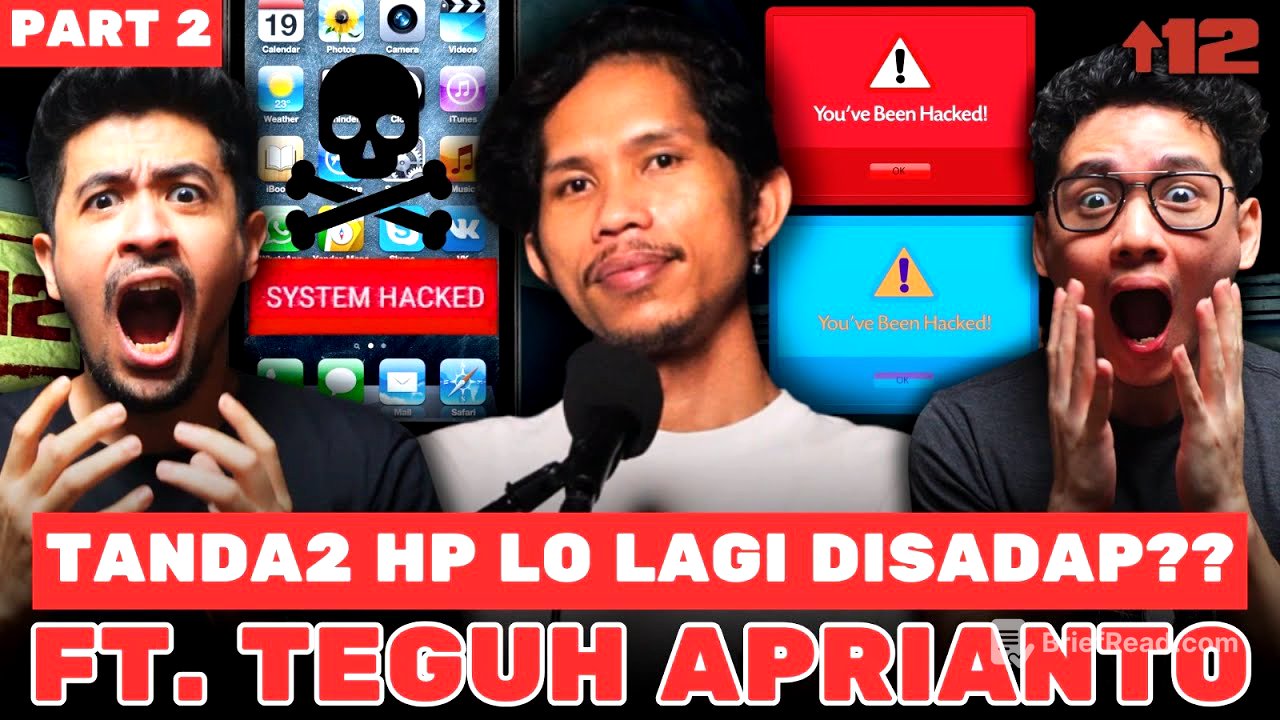
The video starts by introducing the topic of hacking and cybersecurity, mentioning famous hacking tools like Pegasus and discussing the dark web and deep web. The speakers highlight the importance of being aware of potential vulnerabilities and threats in the digital world.
Tapping and Prevention [1:11]
The discussion shifts to tapping, explaining that monitoring data package usage is the easiest way to detect if a cellphone is being tapped. A sudden spike in data usage can indicate unauthorized data withdrawal. The speakers note that there are no preventive measures to avoid wiretapping if someone is specifically targeted, and even high-profile individuals are vulnerable. Regular calls and SMS are not secure, as they can be recorded.
Application Security and SIM Swapping [3:57]
The conversation addresses the security of cellphone applications, emphasizing that there is no guarantee of complete safety due to numerous potential entry points for hackers. Social engineering, especially from close contacts, is a common method of hacking. SIM swapping, a compromise from the provider, is another cheap way to gain access to a victim's accounts by intercepting OTPs.
Secure Messaging Apps [5:11]
The speakers explore the safety of various messaging applications, noting that there is no truly safe Messenger. For sensitive communication, they suggest using apps with auto-delete features. While end-to-end encryption is marketed as a security measure, its reliability is uncertain. They discuss Telegram, WhatsApp, and Signal, explaining that Signal and WhatsApp have similar systems because they share the same creator, while Telegram is cloud-based.
Data Recovery and Selling Cellphones [6:47]
The discussion touches on data recovery, mentioning that even deleted data can sometimes be recovered from memory cards. Selling used cellphones is discouraged because even after a factory reset, data can still be recovered. It is recommended to sell cellphones on marketplaces with anonymous accounts and to avoid informing personal social media about the sale.
Meta's Practices and Conspiracy Theories [10:23]
The speakers criticize Meta's privacy practices, highlighting how the company has used various methods to monitor competitors and collect user data. One unique method involved buying an Israeli VPN company to monitor Snapchat. They debunk the conspiracy theory that cellphones listen to conversations, explaining that targeted ads are a result of location data and friend interactions.
Data Leaks and Personal Data Protection [17:50]
The dangers of data leaks are discussed, noting that they provide criminals with more information about potential victims. It is important to ask what data is for when providing personal information. The speakers mention GDPR in Europe and PDP in Indonesia as laws designed to protect personal data.
iPhone vs Android Security [20:26]
The video compares the security of iPhones and Android devices, stating that neither is guaranteed to be safe, especially when targeted. iPhones are generally considered more secure because they do not allow the installation of applications from outside the App Store. Android devices are more vulnerable due to the ability to install apps from various sources.
Android Security Tips and Hacking Tools [24:05]
Tips for keeping Android devices safe include using the default setting that prevents the installation of applications from outside the Play Store. The speakers introduce Fliper Zero, a small, affordable hacking tool that can clone signals and be used for various malicious purposes, such as car theft and cloning access cards.
Flipper Zero Capabilities and USB Attacks [27:23]
The capabilities of Fliper Zero are further explored, including cloning RFID, infrared signals, and performing Bluetooth spam. The device can also be used for USB attacks by plugging it into someone's laptop and running commands. The speakers mention other similar tools and the importance of being aware of these threats.
Farad Bag and License Plate Reflectors [33:34]
The discussion introduces the Farad Bag, which blocks signals and can be used for privacy reasons. They also mention license plate reflectors and leaf covers that can be used to avoid being photographed by toll road cameras.
Smallest Hacking Tools and Juicing [36:42]
The smallest hacking tool is identified as a USB cable specifically for iOS, which can be used to remotely manage comments and access devices. The speakers warn against free charging in public spaces, as these cables could be used for "jucking," a type of hacking.
Safest Place to Put Money [39:05]
The video explores the safest places to store money, including banks, e-wallets, crypto, and hard cash. They recommend using banks without digital banking or mbanking to avoid skimming and hacking. Crypto is considered risky due to the potential for loss or theft.
ATM Safety and Two-Step Verification [44:05]
Tips for ATM safety include avoiding quiet places and gas stations, checking the card slot for irregularities, and covering the PIN pad when entering the PIN. The speakers emphasize the importance of activating two-step verification on social media accounts using an authenticator application like Google Authenticator, rather than SMS.
Conclusion [48:49]
The video concludes by reiterating the importance of being careful and taking precautions to protect personal data and avoid becoming a victim of cybercrime. The speakers encourage viewers to activate two-factor authentication and stay informed about the latest security threats.